Micro-SaaS #2, New PoC

In my last post, I wrote about 2 roadblocks that I ran into while developing GhostiFi — my plan was to have instant DNS propagation when changing VPS IP addresses by using Cloudflare as a proxy, and to use Vultr snapshots as the basis for backing up/restoring/migrating OpenVPN servers.
During testing, both concepts, which were pretty much the foundation of the project, didn't work as intended. I found out that Cloudflare free plan can’t proxy VPN traffic (HTTP/HTTPS only), and the Vultr snapshots were slower and less reliable than I had expected.
New PoC
I had to come up with a new plan.
Instead of proxying through Cloudflare, I am just going to use Cloudflare DNS with the lowest TTL (120 seconds), and hope that will be short enough to not cause too much disruption to the user as they switch IP/locations with their GhostiFi VPS VPN.
In addition, I will leave the old server up for 5 minutes after the new server is built to allow time for that 2 minute DNS propagation window to complete.
Instead of using Vultr snapshots, I am going to create a private DigitalOcean Space for GhostiFi users’ OpenVPN configuration files. I will tar, label, and store them after initial OpenVPN server creation, then retrieve and untar those configurations for each server rebuild/migration. Making this step work is important, otherwise the user would have to reinstall all of the clients after every rebuild.
Pseudocode Changes
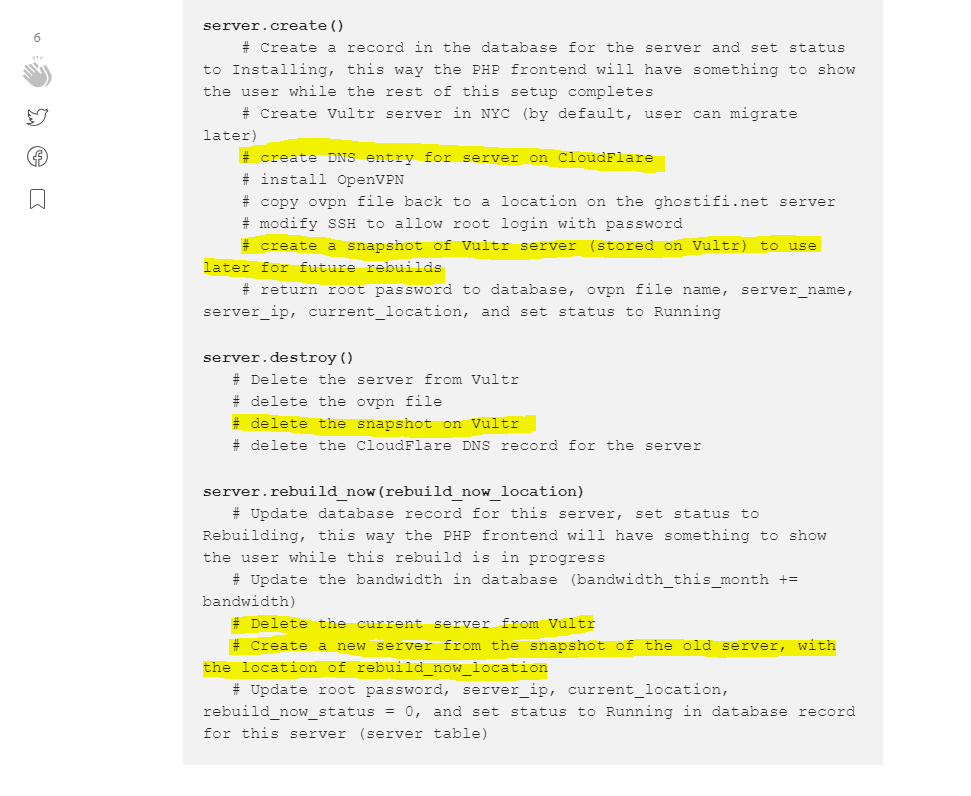
I had to go back to the drawing board and think about what the new pseudocode will look like in order to create the new PoC. Here is what the old pseudocode looks like.
Old Pseudocode
The highlighted areas will need to be changed.
New Pseudocode
Changes are in bold & italic.
server_check.py
# Custom Python class called server which I will create methods "create", "destroy", and "rebuild_now" for
server = server(server_name, username)
# Create a server object with a server_name (g0xxx.ghostifi.net for example, and customer's username)
server.create()
# Create a record in the database for the server and set status to Installing, this way the PHP frontend will have something to show the user while the rest of this setup completes
# Create Vultr server in NYC (by default, user can migrate later)
# create DNS entry for server on CloudFlare, set TTL to 120
# install OpenVPN
# copy ovpn file back to a location on the ghostifi.net server
# modify SSH to allow root login with password
# Tar OpenVPN config files and save to DigitalOcean Space
# return root password to database, ovpn file name, server_name, server_ip, current_location, and set status to Running
server.destroy()
# Wait 5 minutes for DNS propagation, then begin deleting
# Delete the server from Vultr
# delete the ovpn file
# delete OpenVPN config tar from DigitalOcean Space
# delete the CloudFlare DNS record for the server
server.rebuild_now(rebuild_now_location)
# Update database record for this server, set status to Rebuilding, this way the PHP frontend will have something to show the user while this rebuild is in progress
# Update the bandwidth in database (bandwidth_this_month += bandwidth)
# Delete the current server from Vultr
# Create a new server, with the location of rebuild_now_location
# Install OpenVPN
# Download OpenVPN config files from DigitalOcean Space and untar
# Update root password, server_ip, current_location, rebuild_now_status = 0, and set status to Running in database record for this server (server table)Closing thoughts
I’m building GhostiFi completely transparently, sharing the process from concept, to sketch, pseudocode, and finally actual code. I hope this is helpful for anyone who is an aspiring programmer or entrepreneur to follow my journey.
If you have any feedback on GhostiFi or alternative solutions to these problems please let me know in the comments section!
I am also looking for feedback on the concept itself, as well as beta testers. Please sign up for the newsletter at https://ghostifi.net if you are interested.
